Quant Quiz
Directions (Q.1-5): Study the following pie chart carefully and answer the questions given below.
Percentage of people in a city working in night shifts from various industries
(Total number of People = 40250)
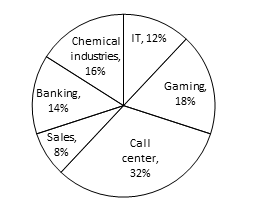
| Industries | Females |
| IT | 20% |
| Gaming | 20% |
| Call center | 45% |
| Sales | 60% |
| Banking | 40% |
| Chemical industries | 15% |
Q1.What is the respective ratio of the men to the women working in night shifts from the call center industry?
(a) 9 : 11 (b) 7 : 5 (c) 8 : 13 (d) 11 : 7 (e) 11 : 9
Q2.What is the approximate average number of females working in night shifts from all the industries together?
(a) 2227 (b) 4481 (c) 3326 (d) 2823 (e) 4107
Q3.What is the total number of men working in night shifts from all the industries together?
(a) 28297 (b) 25788 (c) 28678 (d) 26887 (e) None of the above
Q4.The number of women working in night shifts from the gaming industry is what per cent of the total number of people working in the night shifts from all the industries together?
(a) 5.6% (b) 3.6% (c) 3.2% (d) 4.4% (e) None of the above
Q5.What is the difference between the total number of men and the total number of women working in night shifts from all the industries together?
(a) 13254 (b) 13542 (c) 13524 (d) 13363 (e) None of the above
Directions (Q.6-8): Each question below is followed by two statements I and II. You are to determine whether the data given in the statement is sufficient for answering the question. You should use the data and your knowledge of Mathematics to choose between the possible answers. Give answer
(a)If the statement I alone is sufficient to answer the question but the statement II alone is not sufficient.
(b)If the statement II alone is sufficient to answer the question but the statement I alone is not sufficient.
(c)If both statements I and II together are needed to answer the question.
(d)If either the statement I alone or statement II alone is sufficient to answer the question.
(e)If answer cannot be obtained from the statements I and II together but need even more data.
Q6.What is the salary of B in a group of A, B, C and D whose average salary is Rs. 62880?
I. Total of the salaries of A and C is exact multiple of 8.
II. Average of the salary of A, C and D is Rs. 61665.
Q7.What is the three-digit number?
I.The three-digit number is divisible by 9. II. The first and the third digits are 6.
Q8.What is the profit earned by selling a printer for Rs. 3000.
I. The cost price of 6 such printers is equal to selling price of 5 such printers. II. 20% profit is earned by selling each printer.
Q9.A new flag is to be designed with six vertical stripes using some or all of the colour yellow, green, blue, and red. Then, the number of ways this can be made such that no two adjacent stripes have the same colour is
(a) 12 × 81 (b) 16 × 192 (c) 20 × 125 (d) 24 × 216 (e) None of the above
Q10.A boat running upstream takes 528 min to cover a certain distance, while it takes 240 min to cover the same distance running downstream. What is the ratio between the speed of boat and speed of the water current, respectively.
(a) 2 : 1 (b) 3 : 2 (c) 8 : 3 (d) Couldn’t be determined (e) None of the above
1.e 2.a 3.d 4.b 5.c 6.b 7.c 8.d 9.a 10.c
English Quiz
Directions (Q. 1-5): In the following questions, a sentence has been given with some of its parts in bold. To make the sentence correct, you have to replace the bold part with the correct alternative given below. If the sentence is correct as it is, please give 5) as you answer (ie No correction required).
Q1. There was a question about Napoleon in the exam, thank goodness I brushed over on him.
a) brushed aside on him b) brushed up on him c) brushed on him d) brushed about on it e) No correction required.
Q2. Rajeev is working part time in a factory to put himself on college.
a) put himself in b) put himself about c) put him throughout d) put himself through
e) No correction required.
Q3. The number of tourists begins to taper off in late autumn.
a) taper on b) taper down c) tapering d) taper up e) No correction required.
Q4. The committee rejected the idea at the first, but they are now warming to it.
a) the idea at first b) the idea first c) idea at the first d) ideas about the first e) No correction required.
Q5. Rosa was cautioned by the police and she was scared that news of this would get out in her home town.
a) would get off b) would get up c) would get around d) will get about e) No correction required.
Directions (Q. 6-10): Rearrange the following six sentence (A), (B), (C), (D), (E) and (F) in the proper sequence to form a meaningful paragraph and then answer the questions given below.
(A) But for its survival, it needs food.
(B) This is nature is its true form.
(C) A jellyfish sometimes swallows a snail and since the snail is protected in the shell, it remains alive.
(D) So, it starts eating the jellyfish from inside and keeps growing till it consumes the entire jellyfish.
(E) It is always the enemy within that consumes and destroys society.
(F) It is difficult to change.
Q6. Which of the following would be the FIRST sentence after rearrangement?
a) B b) D c) A d) C e) F
Q7. Which of the following would be the THIRD sentence after rearrangement?
a) C b) D c) A d) B e) E
Q8. Which of the following would be the FIFTH sentence after rearrangement?
a) E b) B c) C d) D e) F
Q9. Which of the following would be the LAST (SIXTH) sentence after rearrangement?
a) D b) A c) E d) B e) C
Q10. Which of the following would be the SECOND sentence after rearrangement?
a) A b) C c) B d) D e) E
1.b 2.d 3.e 4.a 5.c 6.d 7.b 8.e 9.c 10.a
Computer Quiz
Q1. In a word processor application, the user might want to cut text from one part of a document and paste it in another part of the document or somewhere else. When the user copies the selected content, it’s stored in the________
(a) Cache Memory (b) RAM (c) Virtual Memory (d) Clipboard (e) EEPROM
Q2. _____are often used to stop bots and other automated programs from using blogs to affect search engine rankings, signing up for e-mail accounts to send out spam or take part in on-line polls.
(a) Malware (b) Firewall (C) CAPTCHA (d) biometrics (e) Automation
Q3. A_____ application interface directly with users and forward requests to a remotely-located program in another computer to get requested data or perform a requested service.
(a) Front-end (b) Warehouse (c) Back-end (d) Terminal (e) None of these
Q4. 4-D includes the three spatial dimensions plus time , which allows researchers to simulate the progression of a disease or the effects of a treatment over a period of time. The first such model ever developed, _____is known as a 4-D human atlas.
(a) pygmy (b) IGLOO (c) CAVEman (d) NeuroMAN (e) None of these
Q5._____is an example of businesses and government agencies can use central Web sites to exchange information and do business with each other more efficiently than they usually can off the Web.
(a) B2G (b) G2B (c) G2G2C (d) B2G2C (e) None of these
Q6. What term is used to identify people coming together from various geographical locations to complete some task online ?
(a) I-team (b) Virtual team (c) Online work group (d) Distributed team (e) None of these
Q7. Which of the following is Open Source Software?
(a) Windows (b) Linux (c) IOS (d) Adobe Photoshop (e) None of these
Q8. Which of the following is an OLTP program from IBM?
(a) COBOL (b) JAVA (c) RISC (d) CICS (e) None of the above
Q9. A ___________________________ handles an organization’s day-to-day accounting needs; keeping a verifiable record of every transaction involving money, including purchases, sales, and payroll payments.
(a) Online transaction processing system (OLTP) (b) Financial support system (FSS)
(c) Decision support system (DSS) (d) Business processing system (BPS) (e) None of these
Q10. _______ is a security process that relies on the unique biological characteristics of an individual to verify.
(a) CAPTCHA (b) AADHAR (c) PAN CARD (d) BIOMETRICS (e) DNA
Q11. KPO is the allocation of relatively high-level tasks to an outside organization or a different group (possibly in a different geographic location) within the same organization. What is the full form of KPO?
(a) Knowledge Process Outsourcing (b) Knowledge Procedure Organization (c) know process outcomes
(d) Know processing outcomes (e) Knowledge Process Outcomes
Q12. Which of the following character set supports Japanese and Chinese font?
(a) EBCDIC (b) ASCII (c) BCD (d) EDCBI (e) Unicode
Q13. Which of the following is the combination of numbers, alphabets along with username used to get access to a user account?
(a) Password (b) Username (c) Title name (d) Host-id (e) Screen name
Q14. A database, called the _________________, stores configuration information about installed peripherals and software.
(a) BIOS (b) Profile (c) Registry (d) Boot sector (e) None of these
Q15.Networks that use different technologies can be connected by using:
(a) Packets (b) Switches (c) Bridges (d) Routers (e) None of these
S1. Ans.(d)
Sol. A clipboard is a temporary storage area for data that the user wants to copy from one place to another.
S2. Ans.(c)
Sol. A CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) is a challenge-response system test designed to differentiate humans from automated programs.
S3. Ans.(a)
Sol. Relative to the client/server computing model, a front-end is likely to be a client and a back-end to be a server.
S4. Ans.(c)
Sol. CAVEman is an interactive, object-oriented model of a human body consisting of over 3,000 anatomically correct, cataloged and computerized body parts.
S5. Ans.(a)
Sol. B2G may also include e-procurement services. B2G may also include the rental of online applications and databases designed especially for use by government agencies i.e. e-bidding web portals e-Trans and DEEP introduced by GOI is the reverse auction in transmission sector.
S6. Ans.(b)
Sol. Virtual teams are a great way to enable teamwork in situations where people are not sitting in the same physical office at the same time. Such teams are used more and more by companies and other organizations to cut travel, relocation, real estate, and other business costs.
S7. Ans.(b)
Sol. .Linux is can be used for various purposes i.e Web Serving(Nearly 60% of all websites on the Internet are run using an Open Source program named “Apache.”)Networking, Databases, Scientific computing
S8. Ans.(d)
Sol. CICS (Customer Information Control System) is an OLTP program from IBM that, together with the COBOL programming language, has the most common set of tools for building customer transaction applications in the world of large enterprise mainframe computing.
S9. Ans.(a)
Sol. OLTP systems are used for order entry, financial transactions, customer relationship management (CRM) and retail sales. OLTP is characterized by a large number of short on-line transactions (INSERT, UPDATE, DELETE).
S10. Ans.(d)
Sol. Biometric authentication systems compare a biometric data capture to stored, confirmed authentic data in a database.
S11. Ans.(a)
Sol. KPO is, essentially, high-end business process outsourcing (BPO). Examples of KPO include accounting, market, and legal research, Web design and content creation.
S12. Ans.(e)
Sol. Unicode is a computing industry standard for the consistent encoding, representation, and handling of text expressed in most of the world’s writing systems.
S13. Ans.(a)
Sol. A password is an un-spaced sequence of characters used to determine that a computer user requesting access to a computer system is really that particular user.
S14. Ans.(c)
Sol. The registry is a system-defined database in which applications and system components store and retrieve configuration data.
S15. Ans.(d)
Sol. A router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions on the Internet.